Robot System Testing
Testing of Robotic SystemsChallenges and Motivation
There is no systematic way of generating test scenarios for robot applications.
Robot applications are generally more complex in the number of scenarios compared to autonomous vehicles.
Robot vulnerability identification is also a key issue. Nobody worked on this before.
Goals
Non-determinism and Entropy in Robotic Applications/Software
How effective are traditional coverage-based testing?
A good metrics to evaluate mutation?
A good strategy ...
OpenAPI Annotation Design
OpenAPI Annotation DesignGeneral DesignBackgroundExisting Problems and Challenges:
API Coverage:
Some parameters are almost impossible to generate randomly
Some API operations are critical in terms of logic (login, checkout, etc.), and cannot be arbitrarily called.
Resources are created on each run with very low efficiency
Multi-API vulnerabilities are not considered and discussed.
Goal: Annotate the original OpenAPI specification to guide the API fuzzing process, so that
Multi-API vu ...
Cloud Robotics Study
Cloud Robotics StudyABI Research Report: Cloud Robotics
Why cloud robotics?
Developers can offload the computational heavy tasks to cloud. As robot systems scale, this becomes extremely important.
Companies turn to cloud-based services to expand their offering in value-added services.
Robotics systems key functions
Services vs. Cloud
Most robotics companies with cloud-robotics projects are working closely with military.
A Survey of Research on Cloud Robotics and AutomationCloud Roboti ...
SROS Protocol Model Checking
SROS Security through Model CheckingThe goal of this work is to thoroughly identify the security problems in SROS communication. To do this, we use model checking method with the assist of tool event-b.
One of the useful paper: https://www.iiitb.ac.in/SELab/preprints/TR_IoTProtocolModel.pdf
The links to learn event-b: https://blog.csdn.net/Campsisgrandiflora/article/details/113575445?utm_medium=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7EBlogCommendFromMachineLearnPai2%7Edefault-1.co ...
ROS2 Boardcast Encryption Design
SROS2 Broadcast Encryption System DesignRandom Ideas / Brainstorming[21/05/2021]
Maintain one keystore that contains public key for all users
Each node should have access to its own public key (cert) and private key
To-dos: understand existing x509 key encryption/decryption. Source: Github Repo on M2Crypto
[22/05/2021]
Datatype handling: in ROS2, the datatype of a publisher/subscriber should be pre-defined. However, the transmitted message cannot be in random datatype. In case that publishe ...
REST API Security Testing Implementation
API Security TestingOWASP API Security Top 10 [link]
API1:2019 Broken Object Level Authorization
APIs tend to expose endpoints that handle object identifiers, creating a wide attack surface Level Access Control issue. Object level authorization checks should be considered in every function that accesses a data source using an input from the user.
API2:2019 Broken User Authentication (This one requires manual checking)
Authentication mechanisms are often implemented incorrectly, allowing attac ...
ABE in Multi-Robot Systems
Access Control in Multi-Robot SystemsSummaryMay refer to IoT device for access control examples.
PapersPolicy-Based Access Control for Robotic Applications [link]An add-on node layer to achieve policy-based access control for ROS1
No threat model. “The goal is to design an access control system for robots”.
Use access manager to manage the policies; all requests to resources should go to manager.
Procedurally Provisioned Access Control for Robotic Systems [link]Main contribution: “a set of tool ...
[HTB Hints] Academy
Coming back to HTB and practice pentest skill :D. The machine Academy is still active so only the brief ideas are listed here.
ReconNmap and identify the only open port 80. Set domain name properly to access the content. Use dirbuster to fuzz web pages.
Initial AccessTwo webpages appears to be pretty interesting: /admin.php and /login.php. Reading the source code of registration page it is easy to register for an admin access user.
UsersSet domain name again based on admin page contents. Read t ...
work plan
Workplan11/01/2020Robotics
Assemble the three robots
Make the three robots work together in the environment.
Implement RRT exploration algorithm in real-world environment
Record the simulation experiment result with time series
do more records to cover the original experiment result
Repeat the experiment in real-world (exploration, for example) [exploration for m-explore package tested]
Find good ways to monitor simulation system performance.
One possible way to monitor the system per ...
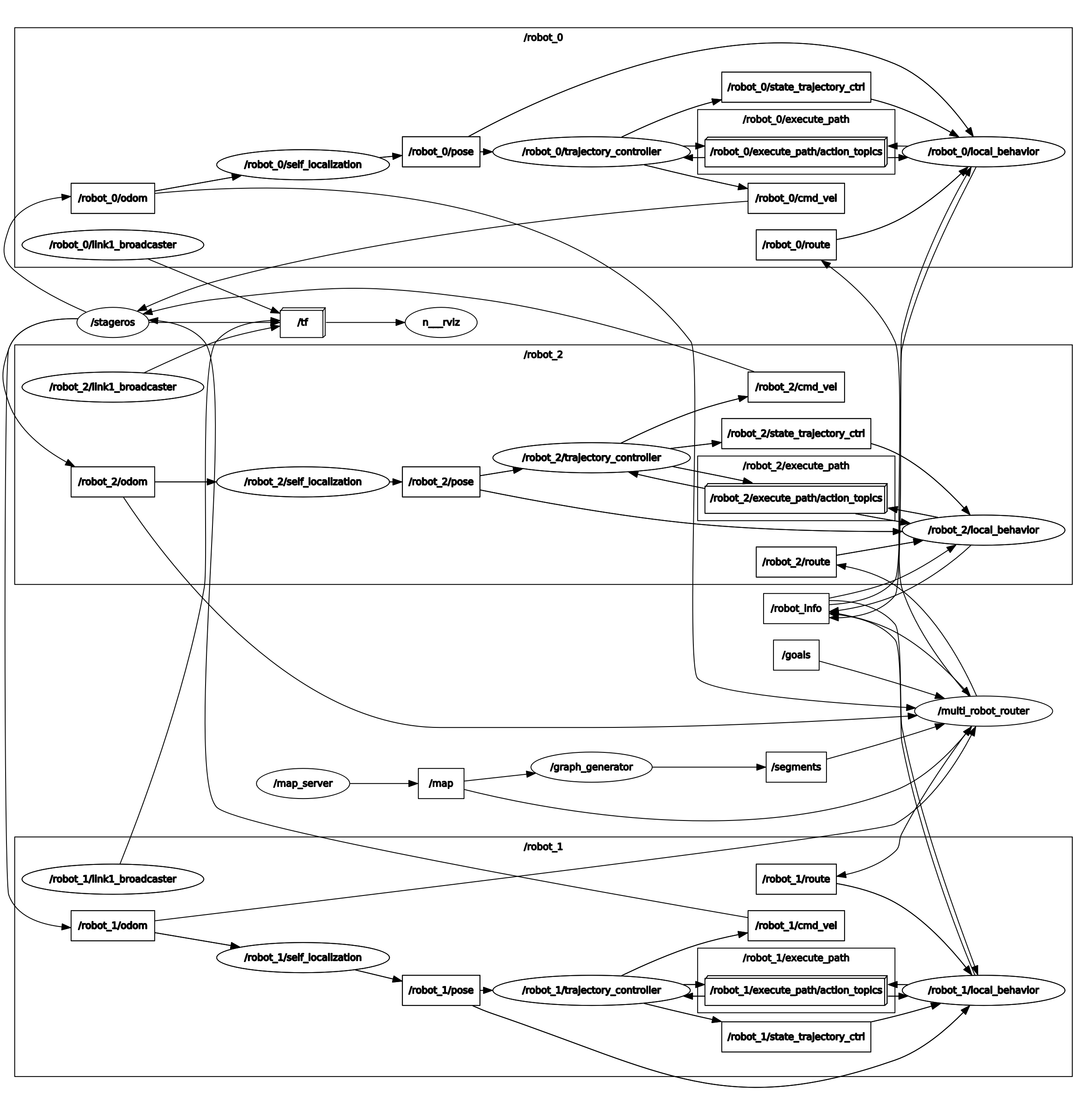
Multi-Robot System Research
TUW Multi Robot NavigationOverview
Documentation: https://repositum.tuwien.at/bitstream/20.500.12708/2982/2/Spatio-temporal%20prioritized%20planning.pdf (This is a master thesis)
Key InfoIn this navigation design:
No communication between robots. All controls are done by the controller.
Not sure if there’s local object avoidance function. Will check on it.
Key message type, robot_info is documented here: http://docs.ros.org/melodic/api/tuw_multi_robot_msgs/html/msg/RobotInfo.html
Outbound/robo ...



![[HTB Hints] Academy](https://www.yeahhub.com/wp-content/uploads/2018/03/hackthebox.png)