Access Control in Multi-Robot Systems
Summary
May refer to IoT device for access control examples.
Papers
Policy-Based Access Control for Robotic Applications [link]
An add-on node layer to achieve policy-based access control for ROS1
No threat model. “The goal is to design an access control system for robots”.
Use access manager to manage the policies; all requests to resources should go to manager.
Procedurally Provisioned Access Control for Robotic Systems [link]
Main contribution: “a set of tools to provide users with an automated approach for systematic generation and verification of necessary cryptographic artifacts in a familiar, yet extendable, meta-build system layout via workspaces and plugins”.
Two main components. ComArmor: a profile configuration language to define Mandatory Access Control (MAC) policies for communication graphs. Keymint: generating cryptographic artifacts used in securing middleware systems like ROS, DDS, etc.
The evaluation process is relatively naïve. The author created an unsecured ROS2 semantic graph model, and use the proposed method to implement the access control.
Cybersecurity of Robotics and Autonomous Systems: Privacy and Safety
This work presents a survey on the cybersecurity attacks associated with services robots.
- Robotic security: virtual and physical. In this work, privacy and safety are primarily concerned.
- Safety: mainly on physical risks
- Privacy: The mis-usage of multiple sensors (camera, microphone, etc.)
Security for the Robot Operating System [link]
Addressed three attack vectors on a ROS-application:
- Unauthorized Publishing (Injections)
- Unauthorized Data Access
- Denial of Service (DoS) attacks on specific ROS nodes.
Rogue Robots: Testing the Limits of an Industrial Robot’s
Security [link]
Industrial research paper
5 attack approaches: Altering the Control-Loop Parameters, Tampering with Calibration Parameters, Tampering with the Production Logic, Altering the User-Perceived Robot State, Altering the Robot State
Attack surface analysis: Physical, local, remote, wireless
Rethinking Access Control and Authentication for the Home Internet of Things (IoT) [link]
Consider why IoT device need access control => similar concept to robots system
Survey with 450 participants to discover the needs and concerns for IoT device
An access control approach based on the capability of device.
The proper authentication method that balances convenience and security
Attribute-based Encryption
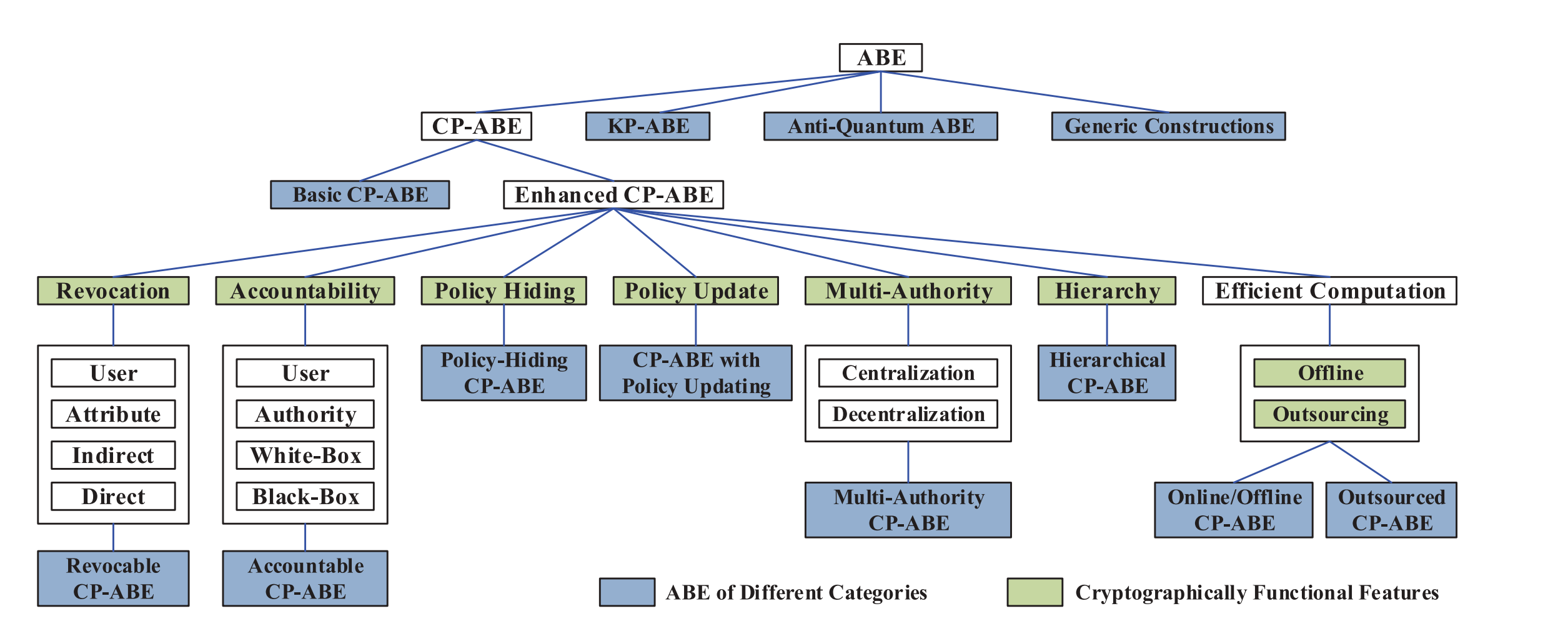
Ciphertext-Policy ABE (CP-ABE)
A ciphertext can be decrypted by a user if and only if the user’s attribute list matches the ciphertext’s access policy.
- Application scenario: Basic fine-grained access control. Four parties: cloud service provider (CSP), attribute authority (AA), DO, DU.
Key-Policy ABE (KP-ABE)
ROS2 Access Control Designs
useful Links
github links: ros2_access_control_policies
github_links: ros2_dds_security
Procedures to Implement ROS2 Access Control
The implementation of this section can refer to here. SROS2 create relatively easy cmd tools to create rules and policies.
Assume that we are developing a multi-robot system different nodes running on different machines.
Authentication
- Define a Certificate Authority (CA) that generally owns the system. Create a keystore on the system.
- Key generation: For each node that needs to be authenticated, CA generates key pairs for it. The key should then be distributed to the node owner (on different machines).
- Authentication: Nodes are authenticated by the certs.
Access Control
- Define the security policies, and update policies through command line. The permissions are written by permission.p7s and permissions.xml file.
- Distribute the permissions files to the target machine.
- Assign the rules defined in policy xml file. The command
ros2 security create_permission <keystore> <node_names> policy_names - Run the nodes
Remaining problems to solve:
- Who defines access control?
Drawbacks of Existing ROS2 Access Control
- Implementation Issue: nodes crash in case of access violation (not errors or warnings).
ABAC vs RBAC: the problem is why to use ABAC in robotic systems.
The main drawbacks of existing robotic system access control methods:
- Not dynamic: the access is only checked at the joining of a node. Once the node starts, flushing access control will not cause the existing nodes to drop connections. There are multiple robots joining/exiting the large scale factories every day.
- Robots authentication/access control cannot be configured on a time-basis. (Ideally it is possible to create a certificate that expires after certain time, but this function is not seen in SROS2).
Multi-Robot Security Related News
- Security for multirobot systems: New technique could protect robot teams’ communication networks from malicious hackers.
- Various ROS and ROS2 implementation by AmazonRobotics
Authentication Implementation in ROS2: ECDSA
Some details about elliptic curve digital signature algorithm: wiki
More reading materials: doc
- public-secret keys generation
- Definition of the elliptic curve function
- Use elliptic curve for secret sharing and authentication
ProVerif Usage
Check official manual; install through opam on Linux system is the most convenient method.
ProVerif on ROS2
Consider a broadcast communication channel based on publisher-subscriber structure
No auth, no access control
1 | free c:channel. |
With Auth, no access control, attacker outsider
1 | type random. (* random number : 128 bitstring *) |